Index
SNMP v3 Overview
In addition to all functionality available via SNMP2, SNMPv3 supports authentication and encryption but at the cost of network load and server performance. SNMPv3 utilizes a user-based security model (USM) for message security, and a view-based access control model (VACM) for access control.
USM implements a ‘user’ for both the SNMP agent and the SNMP manager. Each user has a range of security parameters (authentication protocol, encryption method, keys, etc) specified. Messages exchanged between the manager and the agent can have data integrity checking and data origin authentication. USM protects against message delays and message replays by using time indicators and request IDs.
To complement the USM, SNMPv3 uses the VACM, a highly granular access-control model for SNMPv3 applications. Based on the concept of applying security policies to the name of the groups querying the agent, the agent decides whether the group is allowed to view or change specific MIB objects. VACM defines collections of data (called views), groups of data users, and access statements that define which views a particular group of users can use for reading from, and writing to, a device.
Statseeker supports:
- Authentication – username-only, SHA, and MD5
- Privacy – AES (128, 192 , and 256), DES, and Triple DES
- Context – a single context
Statseeker supports the following configurations when communicating with SNMPv3 devices:
| Authentication | Privacy | Context |
| None | None | No |
| Yes | ||
| Username-only | None | No |
| Yes | ||
| MD5 | None | No |
| Yes | ||
| DES | No | |
| Yes | ||
| AES | No | |
| Yes | ||
| SHA | None | No |
| Yes | ||
| DES | No | |
| Yes | ||
| AES | No | |
| Yes |
Adding a Single SNMPv3 Device
To add an SNMPv3 device:
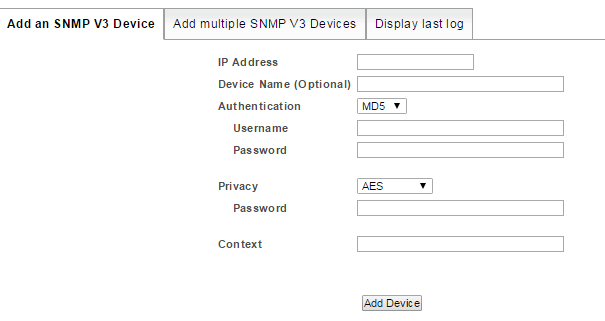
- Select Administration Tool > Network Discovery > Add SNMP V3 Devices
- Specify the:
- IP Address
- Device Name: if used, the name will be added to the Hosts File. If your specified naming scheme (see Administration Tool > Network Discovery – Advanced Options > Advanced Options) doesn’t preference the Hosts File, then this name will be overwritten, with the device’s sysName or IP Address (depending on the device manufacturer) on the next discovery/rewalk.
- Authentication method, username and password
- Privacy/Encryption method, username and password
- Context, if it is applicable to your SNMPv3 configuration, otherwise leave it blank
- Click Add Device
The specified device will be walked and the results of the discovery process will be displayed. This log of the discovery process is retained and can be reviewed from the Display Last Log tab.
Adding Multiple SNMPv3 Devices
Multiple SNMPv3 devices can be added at once using a *.csv file detailing the devices using the following format:
- {IP_Address},{Device_Name},{Authentication_Type},{Authentication_Username},{Authentication_Password},{Privacy_Type},{Privacy_Password},{Context}
- e.g.206.45.123.8,Brisbane-rtr-4,md5,MD5Username,password1,aes256,password2,206.45.123.9,Brisbane-rtr-5,sha,SHAUsername,password2,aes256,password2,context1
- The Device Name and Context fields can be left blank, all other fields are mandatory. If Device Name is used, the name will be added to the Hosts File. If your specified naming scheme (see Administration Tool > Network Discovery – Advanced Options > Advanced Options) doesn’t preference the Hosts File, then this name will be overwritten, with the device’s sysName or IP Address (depending on the device manufacturer) on the next discovery/rewalk.
- Adding SNMPv3 monitoring for a large number of devices may negatively impact the performance of your Statseeker server
- Valid Privacy_Type are none, aes, aes192, aes256, des, or des3
Modifying Existing Devices
The form contains a checkbox labelled Modify the configuration of devices that already exist in Statseeker, behavior related to this setting is as follows:
- Unchecked
- If the IP address has not been discovered by Statseeker previously, then the device will be added as an SNMPv3 device
- If the IP address has been previously discovered by Statseeker, then the row will be discarded and the configuration of the existing device will not be modified
- Checked
- If the IP address has not been discovered by Statseeker previously, then the device will be added as an SNMPv3 device
- If the IP address has been previously discovered by Statseeker but is not currently being polled, then the device will be added as a new SNMPv3 device
- If the IP address has been previously discovered by Statseeker but is currently being polled, then the device will be modified and configured as an SNMPv3 device
Adding Multiple Devices
- Prepare and construct the *.csv file as described and save it locally
- Select Administration Tool > Network Discovery > Add SNMP V3 Devices
- Select the Add multiple SNMP V3 Devices tab
- Click Choose File, browse to the saved *.csv file’s location, select it and click OK
- Choose whether to modify existing devices with the contents of the *.csv
- Click Add Devices
The specified devices will be walked and the results of the discovery process will be displayed. This log of the discovery process is retained and can be reviewed from the Display Last Log tab.
SNMP3 Logs
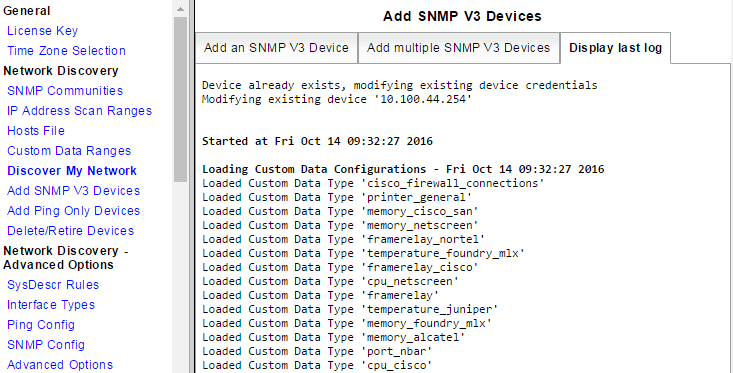
When adding SNMPv3 devices, the results from the process are logged and automatically displayed. A single iteration of the log is retained, with each subsequent process overwriting the old log. Existing logs can be archived and exported for storage via links presented at the end of the log.
The log pertaining to the last time the Add SNMP V3 Devices was run can be viewed from:
- Administration Tool > Network Discovery > Add SNMP V3 Devices > Display last log
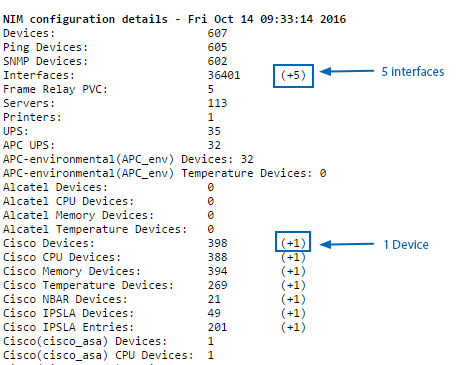
Towards the end of the log there is a section titled NIM configuration details – [date process was run] containing details of those devices newly discovered/configured as SNMPv3 devices.